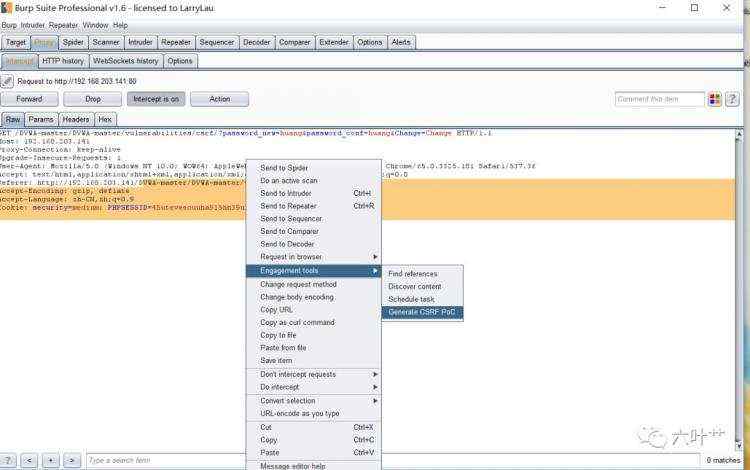
IPSEC野蛮模式:
简介:
IKE 的协商模式
在RFC2409(The Internet Key Exchange )中规定,IKE 第一阶段的协商可以采用
两种模式:主模式(Main Mode )和野蛮模式(Aggressive Mode )。
主模式被设计成将密钥交换信息与身份、认证信息相分离。这种分离保护了身
份信息;交换的身份信息受已生成的 Diffie-Hellman共享密钥的保护。但这增
加了3 条消息的开销。
野蛮模式则允许同时传送与SA、密钥交换和认证相关的载荷。将这些载荷组
合到一条消息中减少了消息的往返次数,但是就无法提供身份保护了。
虽然野蛮模式存在一些功能限制,但可以满足某些特定的网络环境需求。例如:远
程访问时,如果响应者(服务器端)无法预先知道发起者(终端用户)的地址、或
者发起者的地址总在变化,而双方都希望采用预共享密钥验证方法来创建IKE SA,
那么,不进行身份保护的野蛮模式就是唯一可行的交换方法;另外,如果发起者已
知响应者的策略,或者对响应者
本实验采用华为三台F100防火墙,和一台s3526交换机,实现ipsec野蛮模式下的***通道的建立。Fw1是总部,实现fw1可以与fw2的内部网络互访,fw1和fw3的内部网络互访。
拓扑图:
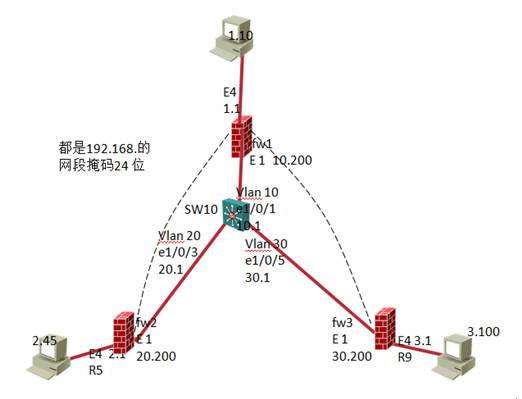
Fw1的配置:
#
interface Ethernet0/1
ip address 192.168.10.200 255.255.255.0
ipsec policy policy
#
#
interface Ethernet0/4
ip address 192.168.1.1 255.255.255.0
ip route-static 0.0.0.0 0.0.0.0 192.168.10.1 preference 60
firewall zone trust
add interface Ethernet0/4
#
acl number 3000
rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule 1 deny ip
acl number 3001
rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule 1 permit ip
#
ipsec proposal tran1 配置安全提议
encapsulation-mode tunnel
transform esp
esp authentication-algorithm md5
esp encryption-algorithm des
display ipsec proposal
quit
#
ipsec proposal tran2
encapsulation-mode tunnel
transform esp
esp authentication-algorithm md5
esp encryption-algorithm des
display ipsec proposal
quit
ipsec policy policy 10 isakmp #ipsec策略配置使用ike协商
security acl 3000
ike-peer peer1
proposal tran1
#
ipsec policy policy 20 isakmp
security acl 3001
ike-peer peer2
proposal tran2
ike local-name fw1
ike local-name fw1
ike peer peer1 配置ike对等体
exchange-mode aggressive
pre-shared-key 1234
id-type name
remote-name fw2
local-address 192.168.10.200
#
ike peer peer2
exchange-mode aggressive
pre-shared-key abcd
id-type name
remote-name fw3
local-address 192.168.10.200
Fw2的配置:
#
interface Ethernet0/1
ip address dhcp-alloc
ipsec policy policy
#
#
interface Ethernet0/4
ip address 192.168.2.1 255.255.255.0
ip route-static 0.0.0.0 0.0.0.0 192.168.20.1 preference 60
firewall zone trust
add interface Ethernet0/4
#
acl number 3000
rule 0 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 1 deny ip
#
#
ipsec proposal tran1
encapsulation-mode tunnel
transform esp
esp authentication-algorithm md5
esp encryption-algorithm des
display ipsec proposal
quit
ipsec policy policy 10 isakmp
security acl 3000
ike-peer peer1
proposal tran1
#
ike local-name fw2
ike peer peer1
exchange-mode aggressive
pre-shared-key 1234
id-type name
remote-name fw1
remote-address 192.168.10.200
#
Fw3的配置:
#
interface Ethernet0/1
ip address dhcp-alloc
ipsec policy policy
#
#
interface Ethernet0/4
ip address 192.168.3.1 255.255.255.0
ip route-static 0.0.0.0 0.0.0.0 192.168.30.1 preference 60
firewall zone trust
add interface Ethernet0/4
#
acl number 3001
rule 0 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 1 deny ip
#
#
ipsec proposal tran2
encapsulation-mode tunnel
transform esp
esp authentication-algorithm md5
esp encryption-algorithm des
display ipsec proposal
quit
ipsec policy policy 20 isakmp
security acl 3001
ike-peer peer2
proposal tran2
#
ike local-name fw3
ike peer peer1
exchange-mode aggressive
pre-shared-key abcd
id-type name
remote-name fw1
remote-address 192.168.10.200
#
交换机的配置:
#
vlan 10
#
vlan 20
#
vlan 30
#
interface Vlan-interface1
ip address 192.168.100.10 255.255.255.0
#
interface Vlan-interface10
ip address 192.168.10.1 255.255.255.0
#
interface Vlan-interface20
ip address 192.168.20.1 255.255.255.0
#
interface Vlan-interface30
ip address 192.168.30.1 255.255.255.0
#
dhcp server ip-pool fw2
network 192.168.20.0 mask 255.255.255.0
gateway-list 192.168.20.1
#
dhcp server ip-pool fw3
network 192.168.30.0 mask 255.255.255.0
gateway-list 192.168.30.1
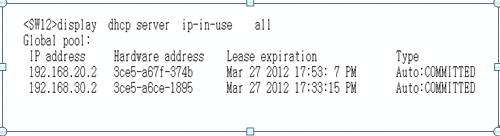
测试:
1.0网段的主机访问2.0和3.0网段的主机:

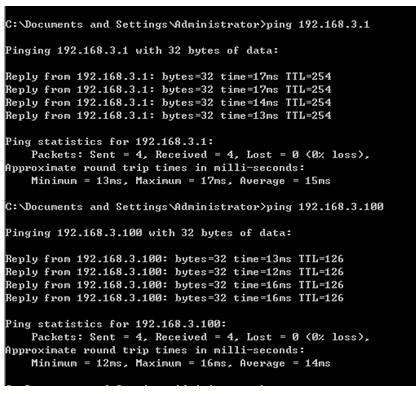
2.0网段的主机访问1.0的主机

3.0网段的主机访问1.0的主机:

此时可以查看相关配置:
查看ipsec sa 已经建立:

查看ipsec policy ,此步配置完即可查看
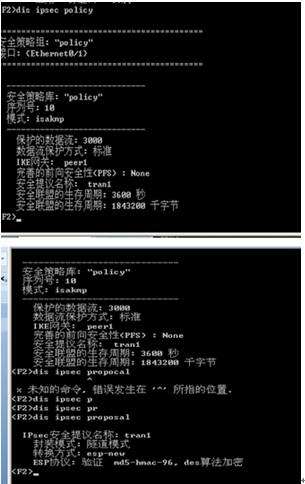





 京公网安备 11010802041100号
京公网安备 11010802041100号